Cybersecurity
Basic Approach
Amid accelerating digitalization and a changing environment for financial services, the posed by cyber threats is growing increasingly serious. To provide safer, more secure services to customers and achieve a society that is resistant to cyber threats, SMBC Group will further strengthen our cybersecurity.
Cybersecurity Management System
Construction of management structure
Viewing cybersecurity risks as one of the top risks faced by our management, we continuously engage in cybersecurity initiatives led by management under our “Declaration of Cybersecurity Management.” Please refer to the bottom of the page regarding the Declaration of Cybersecurity Management.
We manage cybersecurity risks within the framework of company-wide risk management. The Cybersecurity Management Department, a dedicated department for cybersecurity, leads the formulation of basic policy on cybersecurity management, based on the external environment, business strategy, and other factors.
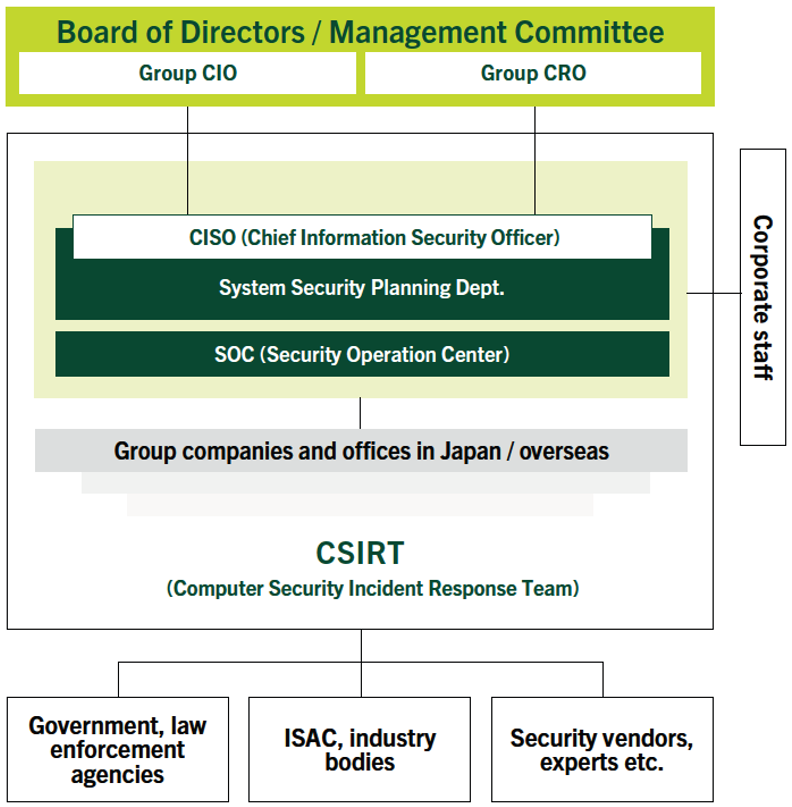
The SMBC Group Management Committee regularly deliberates on cybersecurity management to further strengthen our system on the basis of the basic policy. In addition, the Board of Directors and internal committees such as the Risk Committee and the Audit Committee regularly deliberate cybersecurity management under the supervision of Directors.
To clarify the role of promoting effective cybersecurity measures, we have established the position of Group CISO*1 under the Group CIO and CRO. As the party responsible for general oversight of cybersecurity, the Group CISO engages in supervision and guidance for the development of Group and global system and the promotion of measures at sites from a professional perspective. Additionally, under the leadership of the Group CISO, we have appointed Group Vice CISOs and Regional CISOs, and have established a cybersecurity management structure encompassing over 700*2 cybersecurity professionals on a Group and global basis.
- *1:Chief Information Security Officer
- *2:As of the end of March 2025
Identification of cybersecurity risks
We conduct identification of cyber threats through means including evaluations of cybersecurity-related structures. Specifically, we undergo regular third-party evaluations of the degree of maturity of our security countermeasures, based on international standards.
We also make active use of threat intelligence to respond to the latest cyber threats. We collect and evaluate information on matters including attack trends, vulnerabilities and geopolitical happenings, and apply this to our cybersecurity environment.
In addition, we regularly conduct vulnerability diagnostics to deter damage caused by attacks on vulnerabilities, as well as threat-based penetration testing by which external security experts penetrate actual systems to evaluate security measures.
Based on the internal and external environmental analyses, we identify cyber threats related to our company and strive to further strengthen security measures.
Defense against and detection of cyberattacks
To prepare against unauthorized access, denial of service attacks, and other cyberattacks, we detect and block suspicious communications from the outside through varied security measure services and systems in a multi-layered defense structure.
We have also established a SOC*3, a dedicated organization for network monitoring and analysis, under a 24-hour, 365-day full-time monitoring system. Additionally, through close collaboration with SOCs established in Europe, the U.S., and Asia, we will further strengthen security surveillance on a Group and global basis.
- *3:Security Operation Center
Response to and recovery from cyber incidents
We have established a CSIRT*4 in preparation for cyber incidents.
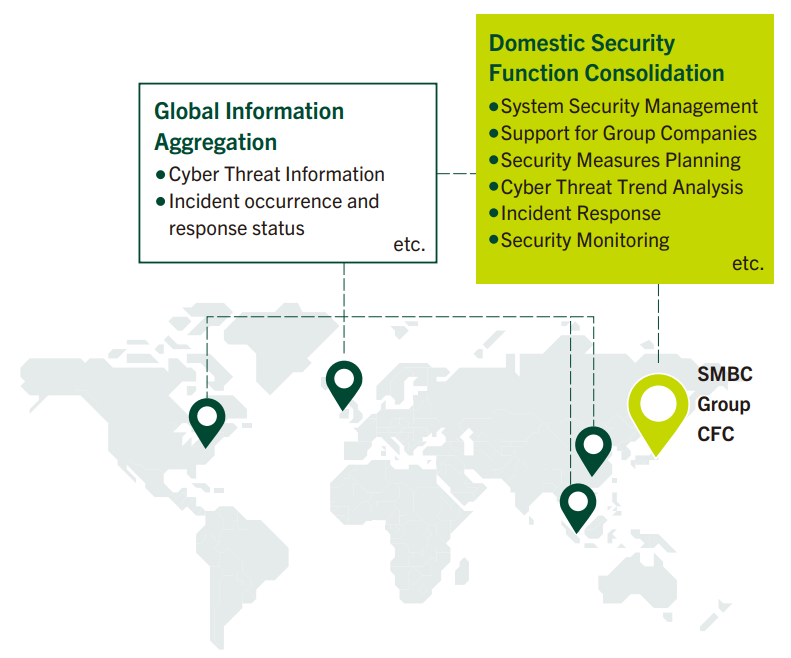
By establishing a Cyber Fusion Center (CFC) that integrates domestic security functions and human resources, we are working to enhance the efficiency of our management system and create an environment enabling quick response to incidents.
The CSIRT actively collects information on attack vectors and on vulnerabilities within and outside the Group, and collaborates with national authorities and bodies such as U.S.-based FS-ISAC*5 and Financials ISAC Japan.
In preparation against attacks, we are working to further strengthen our cyber resilience through regular participation in simulated attack exercises conducted by outside experts and cyberattack response exercises organized by the Financial Services Agency, Finances ISAC Japan, and other bodies.
- *4:Computer Security Incident Response Team
- *5:Financial Service Information Sharing and Analysis Center
Cybersecurity-Related Awareness-Raising Activities and Expert Human Resources
Awareness-raising activities
To foster a culture that enhance awareness of security measures, we conduct awareness-raising activities tailored to roles and responsibilities within the company. For top management, we regularly hold study sessions on topics including management considerations in cybersecurity. For employees, we regularly share messages on cybersecurity from management. In addition, we raise awareness of security through the distribution of educational comics and targeted attack email training and other actions, and use training to instill a “security by design” philosophy for IT system planning staff.
Expert human resources
We recognize that the development of expert human resources is a vital issue in maintaining a medium- to long-term cybersecurity management structure.
We focus on the development of core human resources through the use of internal and external content, the introduction of a program that supports obtaining qualifications, dispatch of staff to graduate schools in Japan and abroad, and participation in specialist organizations and industry associations.
We work to secure expert human resources through mid-career recruitment, and have set up a cybersecurity course for new graduate hires as a part of ongoing structural strengthening.
Declaration of Cybersecurity Management
Sumitomo Mitsui Financial Group “SMFG” and its group companies understand the necessity of “Actively implementing cybersecurity measures from the dual viewpoints of value creation and risk management” which is listed as an important issue by the Japanese Business Federation’s “Declaration of Cybersecurity Management,” and have established our “Declaration of Cybersecurity Management”. We will continue to continually strengthen cybersecurity measures led by executive management to deal with increasingly serious and complex cyber threats.
-
1.Placement of Cybersecurity as a management-level issue
We will take proactive measures regarding cybersecurity from a management-level, and consider cybersecurity as investment in our company. In addition, senior management will continually take steps to understand the latest landscape of cybersecurity, consider cyber threats as one of the major risks facing our group, and manage risks by demonstrating leadership and being directly responsible for security measures.
Specifically, we have defined cyber risk as one of the top risks of SMFG, periodically discuss and review cybersecurity measures at management committees, and assign appropriate resources for project implementation. -
2.Development of management policy and disclosure
We will develop our management policy and incident response structure/business continuity plans by considering not only identification and defense, but also detection, incident management, and recovery. Our management will be proactive in communicating our policy to internal and external stakeholders, and we are active in disclosing our risk management measures and structure in our publicly available disclosure statements.
Specifically, we have a dedicated department for cyber incident response (CSIRT), take appropriate measures to manage threats, and have dedicated policies and manuals in case of an incident. We establish a basic policy for risk management annually, periodically conduct drills, and assess contingency plans. We also disclose our security enhancement policies in disclosure statements. -
3.Establishment of internal/external structure and measures
We distribute appropriate resources internally, implement appropriate physical/technological/personnel security measures, and train our employees in various positions and levels of our group.
In addition, we will take appropriate measures to secure our supply chain, including partners and outsourced companies.
Specifically, we will place necessary personnel in specialized cybersecurity departments, utilize dedicated security education programs to educate employees, and implement the latest technologies to manage security. In addition, we will monitor security at our business partners and outsourcers, and appropriately monitor and manage any vulnerabilities in any assets we procure. -
4.Providing secure systems and services to society
We will implement cybersecurity measures in business activities including system/service development and after release.
Especially, we have implemented security measures in services such as our internet banking through password cards and via our smartphone application, in order for customers to use our services safely with confidence. We also conduct fraudulent activity monitoring. -
5.Contribution to a safe business ecosystem
Through cooperation and collaboration with related regulators, government agencies, and industry bodies, we will proactively share information and contribute to developing professional interpersonal networks within the industry. In addition, we will share information on threats and countermeasures with our customers, contributing to strengthening cybersecurity in society as a whole.
Specifically, we will make timely and appropriate reports government bodies such as the FSA, the National Cybersecurity Office, and the Information-technology Promotion Agency. In addition, we will share information with industry security information sharing bodies such as Financial ISAC, JPCERT, and aim to strengthen our cybersecurity structure globally.